Table of contents
itemis Secure Copy link to clipboard
Data access Copy link to clipboard
The ANALYZE adapter for itemis Secure provides access to any nodes in the resource Document Object Model. The adapter can also access nodes in HTML files.
Configuration Copy link to clipboard
Open the ANALYZE configuration with the ANALYZE configuration editor, and add a new data access as described in section "Data accesses". Select Secure as data access type.
Within the configuration panel, you may specify file patterns consisting of projects, folders or file name patterns which describe the xsam files relevant for analysis.
Supported keywords:
- resource – A pattern for an XML (or HTML) file path.
- URI – A URI to fetch the XML content.
The configuration may contain several resource definitions.
Namespaces are not available in filter expressions and ignored by default. Qualified node and attribute names have to filtered by ‚local-name()’ constraints.
Please note: ANALYZE does not support selection propagation for HTML files and resources in archive files.
Example:
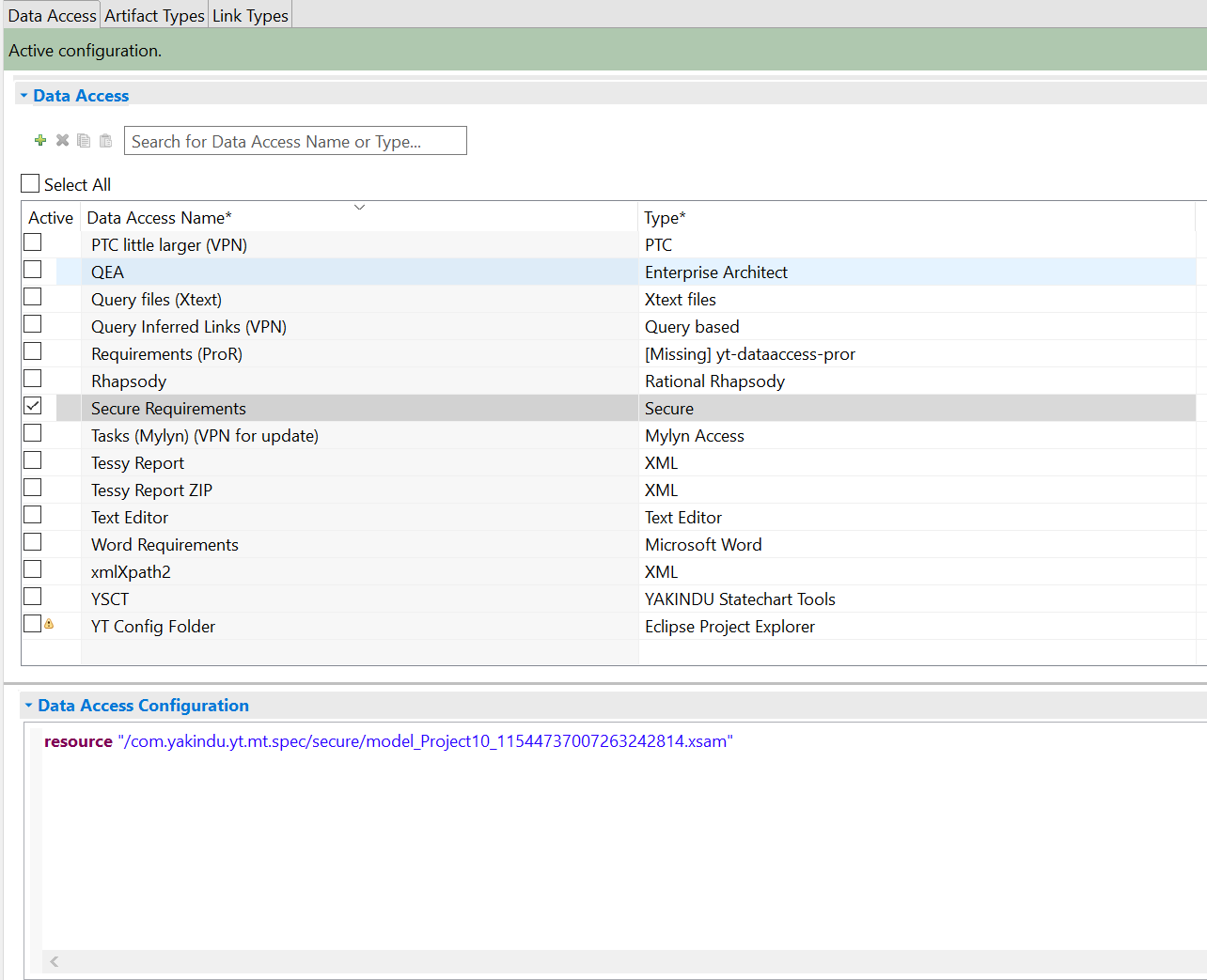
The above configuration tells the adapter to load an Xsam file:
resource "/com.yakindu.yt.mt.spec/secure/model_Project10_11544737007263242814.xsam"
It is also possible to fetch the content via a URI. You see an example for this here:
URI "https://www.example.com/xsam/model.xsam"
Artifact type Copy link to clipboard
This adapter supports the selection of nodes and opening artifacts within the Eclipse XML Editor. The Xsam files have to be defined in the Secure data access.
Configuration Copy link to clipboard
Supported options in the configuration:
- artifact types = ID – The comma separated unique IDs list for Multiple element types can be used in the configuration.
- name – Name for the matched artifact
- identified by – An optional key for an artifact in this document. If specified, it should return a value which uniquely identifies the artifact. If the same value is returned for several Xsam resp. HTML nodes, ANALYZE will only create one artifact.
- map – Starts a mapping block for specifying custom attributes.
- valueOf – XPath expression
-
joined – Follows a
valueOf(
XPath Expression)
statement and allows to join (concatenate) the elements of a list into a single string, separated by the default separator
,. - joined with separator – Follows a valueOf( XPath Expression) statement and allows to join (concatenate) the elements of a list into a single string, separated by the specified separator.
Example:
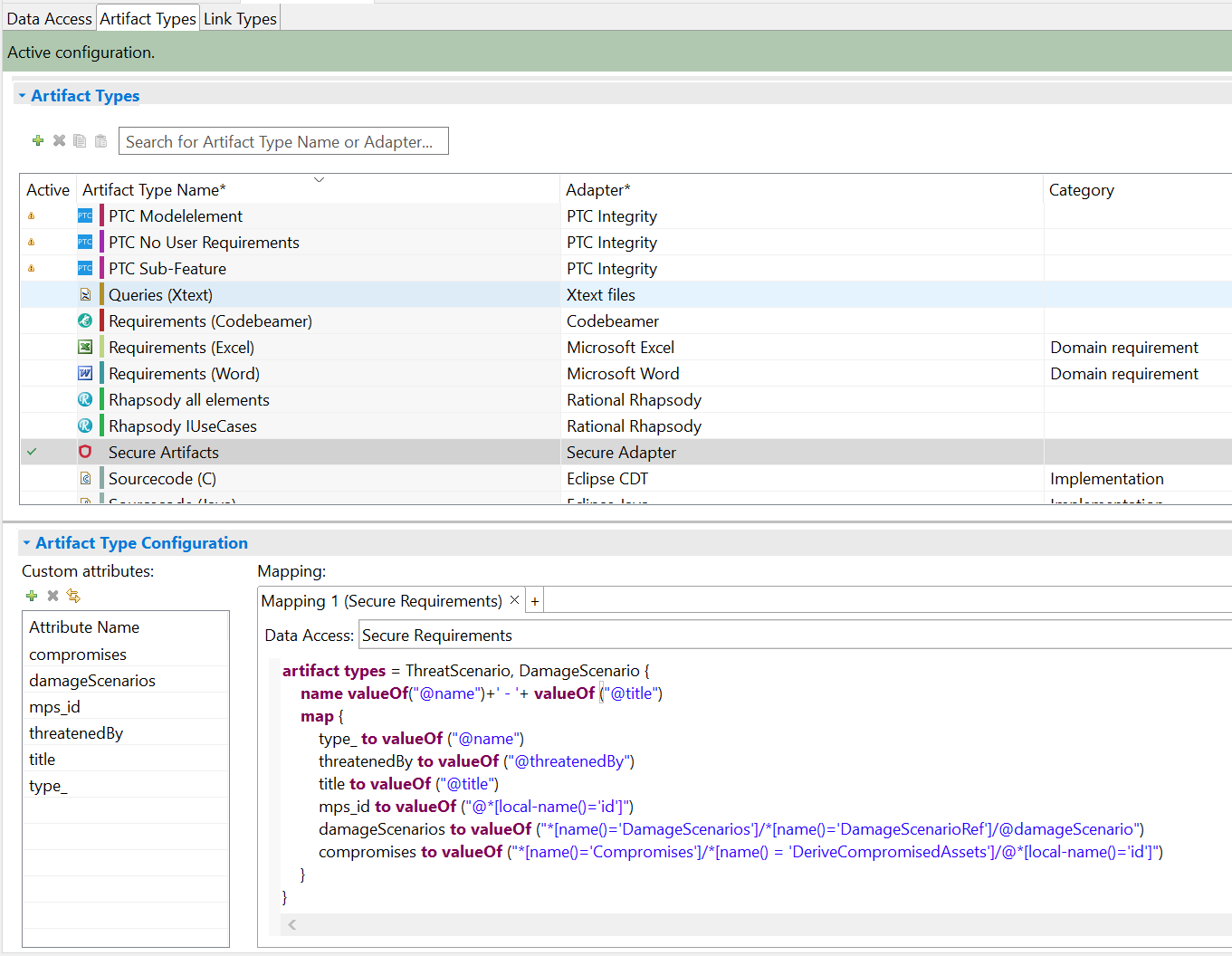
Adapter configuration:
artifact types = ThreatScenario, DamageScenario {
name valueOf("@name")+' - '+ valueOf ("@title")
map {
type_ to valueOf ("@name")
threatenedBy to valueOf ("@threatenedBy")
title to valueOf ("@title")
mps_id to valueOf ("@*[local-name()='id']")
damageScenarios to valueOf ("*[name()='DamageScenarios']/*[name()='DamageScenarioRef']/@damageScenario")
compromises to valueOf ("*[name()='Compromises']/*[name() = 'DeriveCompromisedAssets']/@*[local-name()='id']")
}
}
In the above example, the artifacts will be all ThreatScenario & DamageScenario contained in the Xsam file i.e: One such example for each is :
<ThreatScenario description="" id="6Lgzrm5M$GH" name="TS.2" threatenedBy="AS.2" title="Information Disclosure on ECU">
<CauseOfCompromise>
<ThreatClassRef id="6Lgzrm5M$GM" target="ext/com.itemis.secure/excel/TC.4"/>
</CauseOfCompromise>
<ActedOnTOEEs>
<ComponentRef id="6Lgzrm5M$GG" target="mps/r:8d6fd49d-441f-45f0-ae36-99fae18ef6c8(Project10)/1Xhq32CyUVr"/>
</ActedOnTOEEs>
<CustomImpactCombinator/>
<CustomFeasibilityCombinator/>
<DamageScenarios>
<DamageScenarioRef damageScenario="mps/r:8d6fd49d-441f-45f0-ae36-99fae18ef6c8(Project10)/6Lgzrm5Mu9a" id="6Lgzrm5MHvk"/>
</DamageScenarios>
<Compromises>
<DeriveCompromisedAssets id="6Lgzrm5M$GL"/>
</Compromises>
<Todos/>
</ThreatScenario>
.....
The XPath expressions for name, identified by and mapped attributes will be evaluated against the element for each artifact. So, the expression @title will correspond to the attribute title of the <ThreatScenario> & <DamageScenario> element respectively.
Value references Copy link to clipboard
The name and identified by properties from the previous example are expressed as concatenation of value references:
name valueOf("@name") + "." + valueOf("@title")
The
valueOf keyword introduces a value reference containing an XPath expression. The context of the nested XPath expressions is the matched node from
artifact types. For instance the full XPath expression for
name valueOf("@name") is
"/ThreatScenario/@name", given that only a single
ThreatScenario node is contained in the Xsam document.
If the evaluation of the XPath expression returns a list of elements, it is possible to concatenate the results of this list to obtain a single string attribute. This is achieved using the joined with separator keyword. For instance:
map {
time to valueOf("//ThreatScenario/@name") joined with separator ';'
}
The resulting string will be the concatenation of the time for each testcase contained in the document, separated by semicolon, e.g.,
name1;name2;name3. If the separator is not specified, it defaults to a comma
,.