Table of contents
Create first Project Copy link to clipboard
When creating a new project, the name and location must be specified. Method Configuration and Catalog can be automatically added to the project according to the selected parameters. Predefined method configurations are available for selection. The default configuration is based on the definitions of ISO/SAE 21434. Additional configurations such as Attack Vector / CVSS3.0 and MoRA (Modular Risk Assessment) are available. More custom Method Configurations and Catalogs can be added to a new project via a ZIP archive.
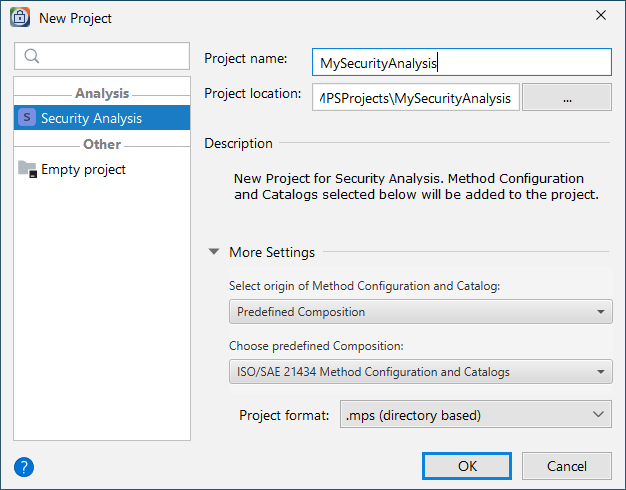
More on Method Configuration and Catalog Copy link to clipboard
A configuration template consists of two main parts, the Catalog and the Method Configuration. All of the elements in it are customizable and extensible.
Threats, controls, and technologies are the contents of the Catalog.
- Threat definitions are based on threat modeling definitions or frameworks for example STRIDE terminology.
- Controls define means of protection against threats (e.g., Spoofing) or protections for cybersecurity properties (e.g., Confidentiality). A control can be for example cryptographic algorithms.
- Technologies can be defined (e.g., CAN) to help the threat analysis.
Method Configurations contain risk, impact and feasibility models for the analysis.
- Risk model contains risk level, risk matrix and risk treatment definitions. Also the rules for propagation options can be customized in this section.
- Impact model contains security properties, impact levels and categories. Additional stakeholders can be added beside the Road User.
- Feasibility model contains the attack feasibility level and feasibility category definitions.
For more detailed information see chapter Method Configuration and Catalogs.