Table of contents
Threat Analysis and Risk Assessment Copy link to clipboard
This chapter provides information for each process step, that is needed as part of a Threat Analysis and Risk Assessment (TARA). The following subsections correspond to these core activities.
The core activities that will be covered are:
- Item Definition
- Trust Analysis (optional)
- Asset Identification and Impact Rating
- Threat Scenario Identification
- Attack Path Analysis
- Risk Determination and Treatment
The elements are organized and stored in so-called chunks. Each chunk is represented by one entry in the project navigation tree and can be organized in folders. Item definition or TARA related chunks can be found in the respective folders. The most important chunks are:
- System Specification chunk: Definition of the system under development (SUD) or item, i.e., Components, Data, Data Flows, Channels, and Functions.
- System Diagram: provides a block diagram editor for the SUD.
- Function Assignment: Matrix to assign functionality to Components, Data, Data Flows, and Channels.
- Security Analysis chunk: Definition of Assumptions, Threat Scenarios, Damage Scenarios, Attack Steps, Controls, Control Scenarios, and Risks.
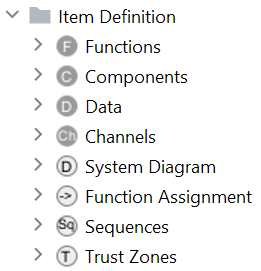
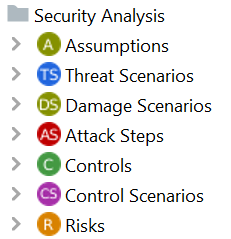
Every element needed for the completion of those activities can be created in the corresponding chunk using the described keyboard shortcut (
Ctrl+Space), the toolbar buttons or the context actions.
Each Security Analysis chunk features a table-like view of its contents. You can change the projection with the toolbar button
Toggle TableView or the key combination
Ctrl+Shift+P.