Table of contents
New Element Types Copy link to clipboard
We’ve introduced new types in accordance with ISO/SAE 21434 to enhance compliance capabilities. All of these types are encapsulated within the "Security Concept” folder.

Requirements Copy link to clipboard
A new chunk reflecting Cybersecurity Requirements has been added. A Requirement can be easily added in the same way as all existing security analysis elements and linked with controls or assumptions.
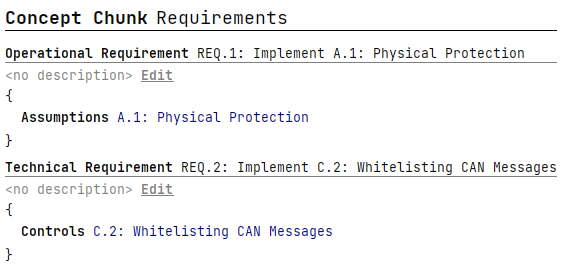
A Requirement consists of a title, name, and a list of elements. The elements can be either Assumptions or Controls. A Requirement has two types, "Operational" and "Technical", determined by the type of elements it contains. An Operational Requirement references Assumptions, while a Technical Requirement references Security Controls. If a user attempts to add different types of elements to one Requirement, a warning will be triggered.
Note: We recommend using our assistants to derive Requirements from existing Controls and Assumptions instead of crafting them manually.
Goals Copy link to clipboard
A new chunk reflecting Cybersecurity Goals has been added. A Goal can be easily added in the same way as all existing Security Analysis Elements.
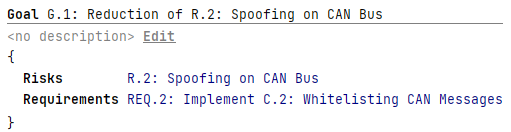
Each Goal comprises a title, name, a list of risks and a list of requirements.
Each assigned risk should be a risk that has been treated as “Reduced” 1 in the Risk Treatment chunk; otherwise, a warning will be triggered. Only technical requirements should be assigned to a Goal; otherwise, a warning will be triggered. Cybersecurity Assurance Level (CAL), cause of compromise, and other details are available in the inspector.
Note: We recommend using our assistants to derive Goals from reduced Risks instead of crafting them manually.
Claims Copy link to clipboard
A new chunk type reflecting Cybersecurity Claims has been added. A Claim can be easily added in the same way as all existing security analysis elements.
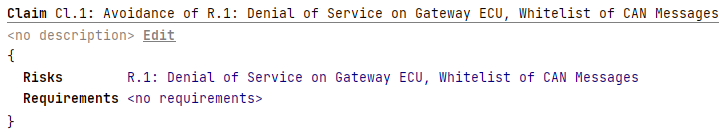
Each Claim comprises a title, name, a list of risks and a list of requirements.
Each assigned risk should be a risk that has been treated as “Shared, or Retained” 1 in the Risk Treatment chunk; otherwise, a warning will be triggered. Only Operational requirements should be assigned to a Claim; otherwise, a warning will be triggered. Cybersecurity Assurance Level (CAL), cause of compromise, and other details are available in the inspector.
Note: We recommend using our assistants to derive Claims from shared or retained Risks instead of crafting them manually.
Security Concepts Copy link to clipboard
A new chunk type reflecting Cybersecurity Concepts has been added. A Concept can be easily added in the same way as all existing security analysis elements.
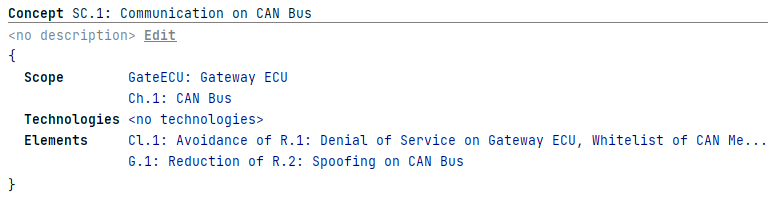
Each Concept comprises a title, name, a Scope (in the form of a list of System Elements), and a list of Technologies, a list of elements (Goals or Claims).
If neither a Scope nor a single Technology is given, the Concept is not limited to a specific subset of all Goals and Claims and is implicitly meant to cover all Goals and Claims.
Note: We recommend using our assistants to populate the Security Concept based on the given scope instead of assigning Goals and Claims manually.
1 While “Reduced, Shared, Retained" is the official ISO terminology, itemis SECURE offers “Avoidance, Reduction, Acceptance, and Share or Transfer” in accordance to the workflow of our clients. Furthermore, you can add any custom treatments.